CI/CD refers to the integrated practices of continuous integration and either continuous delivery or continuous deployment. The CI/CD methodology enables enterprises to bridge the gap between development and operation activities via automation when building, testing and deploying applications.
However, a vital aspect of the pipeline that is often overlooked is security. Here, in this blog, we’ve discussed three important ways to ensure CI/CD security. Let’s take a look!
The process of Continuous Integration and Continuous Deployment enables DevOps teams to deploy application updates into production thus allowing enterprises to reduce costs, prevent risks in the development cycle and increase the delivery rate.
Automating CI/CD pipelines provides developers with more time to build high-quality apps and deliver apps at a faster rate. CI is a software development methodology wherein code changes are made frequently and in a secured manner. Automated build-and-test steps triggered by CI ensure that code changes being pushed into the repository are reliable.
Later, the code is delivered and deployed seamlessly which is a part of the CD process. To sum it up, CI/CD is an automation process that enables incremental code changes from developers’ workstations to be delivered quickly and reliably to production.
According to the 2020 Global DevSecOps Survey, the process of CI/CD eases the tasks of the development team by reducing manual and time-consuming tasks involved in the development process.
For a seamless and secured CI/CD delivery, it’s important for teams to have a good knowledge of what is CI/CD tools and how choosing the right tools and platforms can contribute to a successful pipeline delivery.
Best Practices for ensuring Pipeline Security!
While CI/CD can improve the efficiency of an organization, there are many security considerations that are important for you to take into account. Once CI/CD security is ensured, only then, enterprises can reap the maximum benefits of a CI/CD pipeline. Here are three tips for ensuring pipeline security.
Identify threats and Secure Connections!
While building a secured build and deploy pipeline, it’s essential to first identify the potential security threats. Additionally, the DevOps team must find the vulnerable points that exist within the CI/CD pipeline. This enhances the overall security of the pipeline and keeps it protected from external attacks.
Every connection to the CI/CD pipeline is a point exposed to damaging vulnerabilities and serious threats. Thus, it becomes important for the team to scan all devices, check different parts connected to the pipeline and block devices that fail to meet the set standard security requirements.
Tighten Access Control!
It’s crucial to establish access control rules for restricting access of components to the pipeline. DevOps team should have a clear understanding of what, when and how events are occurring within the pipeline. Comprehensive monitoring, continuous logging and comprehensive observability should be an integral part of the deployment of CI/CD pipelines. Apart from this, in-depth knowledge of what is CI/CD tools is a must to ensure secured deployment.
Conducting automated CI checks and CI analysis can help in preventing the exposure of pipelines to attacks. Developers must implement two-factor authentication and signed commits for preventing high risk. Defining secured access policies help to ensure that only those developers who have valid access credentials can work with code repositories.
Secret Management
Secrets are authentication credentials like usernames and passwords, API tokens, SSH keys, encryption keys that restrict and authenticate access to applications and services. Secrets are an important key to accessing the data of a project and hence managing secrets has become a serious concern for enterprises to resolve security issues.
Secrets management refers to the methodologies and tools used to manage digital authentication credentials known as secrets such as passwords, keys, APIs, and tokens for use in applications, services, sensitive data and private accounts and other confidential parts of the IT ecosystem.
In case these credentials are misused, this can cause a serious data breach of sensitive data. The security team must know and control how, to whom and to what the credentials have been assigned with a well-governed key management service.
By integrating these DevSecOps features in the build & deploy pipelines, businesses can easily prevent high risks and ensure a secured and hassle-free delivery. Besides these practices, in order to enable a seamless and secured CI/CD delivery, it’s important for teams to have a good knowledge of what is CI/CD tools and how choosing the right tools and platforms can contribute to a successful pipeline delivery.
One such Microservices management platform that can help enterprises with a smooth and quick set-up of CI/CD pipelines could be BuildPiper!
How can BuildPiper help?
BuildPiper assists in building CD pipelines enabled with comprehensive CI analysis and customizable CI gate checks for Macro & Micro builds and deployments. With its ability to run zero-touch, fully -automated & secured build & deploy pipelines, BuildPiper helps in making Kubernetes- Microservices application ready. Other security features of this robust platform include,
Automated CI Checks
BuildPiper enables automated and highly intuitive CI checks that support multiple language configurations. With BuildPiper, DevOps teams can override language rules for CI checks. BuildPiper provides tools and configurations for languages that include,
– Java
– Python
– Node
– PHP

Comprehensive CI Analysis
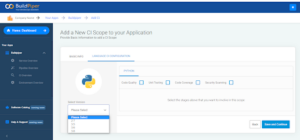
BuildPiper supports comprehensive CI analysis enabling a secure and smooth code release. Users can choose multiple stages while adding a new CI Scope. These stages include,
– Code Quality
– Unit-Testing
– Code Coverage
– Code Security
Support for ISTIO setup and ISTIO gateways!
BuildPiper provides full support for ISTIO setup and ISTIO gateways. With this powerful Microservices DevSecOps Platform, DevOps teams can leverage the out-of-the-box capabilities of ISTIO for traffic management.
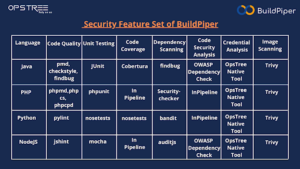
BuildPiper uses the following frameworks and tools for CI analysis in different languages.
Explore and know more about the other interesting features of this robust Microservices DevSecOps platform including Managed Microservices, Managed Kubernetes and Security, Observability & Compliance. Schedule a demo today!